Tcp Port Blocker Tool
The trick to assessing your overall network security is interpreting the results you get from a port scan. You can get false positives on open ports, and you might have to dig deeper. For example, User Datagram Protocol (UDP) scans are less reliable than Transmission Control Protocol (TCP) scans and often produce false positives because many applications don’t know how to respond to random incoming UDP requests.A feature-rich scanner such as QualysGuard often can identify ports and see what’s running in one step.An important tenet to remember is that you need to scan more than just the important hosts. Also, perform the same tests with different utilities to see whether you get different results.
Traktor pro 2 layout downloads torrent. This program sets a new standard for creativity, reliability and pure power of computer DJs. It is based on 4 virtual dishes and a virtual mixer from Allen & Heath Xone 9. Download Crack Traktor Pro 2 Crack Full Mac + Windows Torrent Free DownloadTraktor Pro 2 Crack is the latest incarnation of DJ software that is often referred to as the industry standard. With a complete series of new features, improvements, and innovations.
If your results don’t match after you run the tests using different tools, you might want to explore the issue further.If possible, you should scan all 65,534 TCP ports on each network host that your scanner finds. If you find questionable ports, look for documentation that the application is known and authorized. It’s not a bad idea to scan all 65,534 UDP ports as well. Ping sweepingA ping sweep of all your network subnets and hosts is a good way to find out which hosts are alive and kicking on the network. A ping sweep is when you ping a range of addresses using Internet Control Message Protocol (ICMP) packets.Services or applications that the hosts may be runningAfter performing a generic sweep of the network, you can dig deeper into specific hosts you find.
Block Udp Port
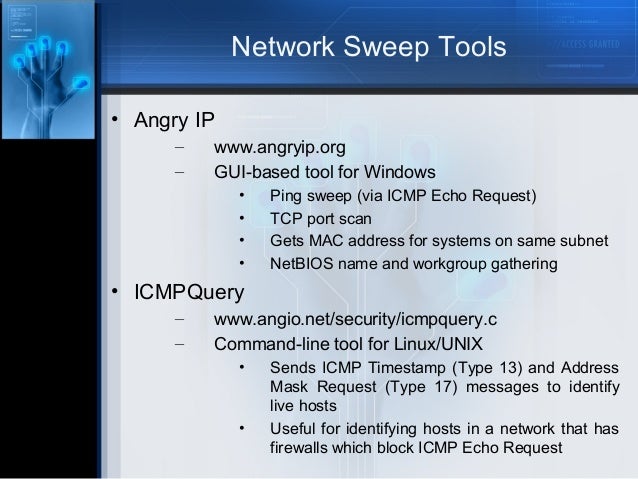
NmapAfter you have a general idea of what hosts are available and what ports are open, you can perform fancier scans to verify that the ports are actually open and not returning a false positive. Nmap allows you to run the following additional scans:.Connect: This basic TCP scan looks for any open TCP ports on the host. You can use this scan to see what’s running and determine whether intrusion prevention systems (IPSs), firewalls, or other logging devices log the connections.UDP scan: This basic UDP scan looks for any open UDP ports on the host. You can use this scan to see what’s running and determine whether IPSs, firewalls, or other logging devices log the connections.SYN Stealth: This scan creates a half-open TCP connection with the host, possibly evading IPS systems and logging. This is a good scan for testing IPSs, firewalls, and other logging devices.FIN Stealth, Xmas Tree, and Null: These scans let you mix things up by sending strangely formed packets to your network hosts so you can see how they respond. These scans change around the flags in the TCP headers of each packet, which allows you to test how each host handles them to point out weak TCP/IP implementations as well as patches that might need to be applied.You can create your own DoS attack and potentially crash applications or entire systems. Unfortunately, if you have a host with a weak TCP/IP stack, there’s no good way to prevent your scan from creating a DoS attack.
To help reduce the chance of this, slow Nmap timing options when running your scans.If you’re a command line fan, you see the command line parameters displayed in the lower-left corner of the NMapWin screen. This helps when you know what you want to do and the command line help isn’t enough.NetScanTools Prois a very nice all-in-one commercial tool for gathering general network information, such as the number of unique IP addresses, NetBIOS names, and MAC addresses.
It also has a neat feature that allows you to fingerprint the operating systems of various hosts.Countermeasures against ping sweeping and port scanningEnable only the traffic you need to access internal hosts — preferably as far as possible from the hosts you’re trying to protect — and deny everything else. This goes for standard ports, such as TCP 80 for HTTP and ICMP for ping requests.Configure firewalls to look for potentially malicious behavior over time and have rules in place to cut off attacks if a certain threshold is reached, such as 10 port scans in one minute or 100 consecutive ping (ICMP) requests.Most firewalls and IPSs can detect such scanning and cut it off in real time.
Even this post is rather old, but it still comes up with the search results so I would like to reply a solution to the question.You can open the Terminal in Mac (type terminal on Spotlight) and then use NetCat command by typing like a sample below to test your specific port like this replacing 1xx with your target IP address, then the port to check.nc -vnzu 1xx.xxx.xxx.xxx 53or if you want to check a range of ports for example from port 1 to 53, just typenc -vnzu 1xx.xxx.xxx.xxx 1-53NetCat is already a built-in command in Mac so no need to install anything.Hope this helps. Welcome to the forums.Common Mac OS X tools used here include Network Utility, lsof, and telnet and ping, and dns-sd and ping for Bonjour and mDNS, depending on details are sought.(With the Windows entries from your footer, various of these tools and equivalents are what can be obtained by loading Cygwin or by loading Microsoft's SUA/SFU tools, and with some add-ons. PowerShell might or does have analogs here, but the old MS-DOS shell was pretty limited in what diagnostics were available without additions. There was telnet and ping, but some other bits were missing.)Add-on tools include nmap. (nmap is a fairly gonzo-useful tool for this sort of thing.)telnet works nicely for brute-force port tests on the LAN.And FWIW, if those public web site tools do work and if you're on your own LAN, then definitely also consider checking the settings of and consider upgrading the LAN security. Those tools and those web sites should be blocked by default by the firewall or the gateway device found on most any LAN; whether that's a low-end NAT device, a server-grade firewall, or otherwise.
If you're trying to figure out whether your client machine is being blocked in the outbound direction (client to Internet) by something like your home firewall, or your ISP, then try.Firebind is the only tool on the Internet that can test any of the 65535 TCP or UDP ports in the outbound direction. If you want, you can test the entire TCP and UDP range.Firebind is sometimes confused with tools like yougetsignal.com, canyouseeme.org, and grc.com which are meant to test inbound connections (from Internet to client machine), usually to validate whether a user has set up their port forwarding rules in their firewall correctly. Other tools like NMAP are port scanners which are designed to probe for open ports on a target machine using a specific IP address.
A port scanner is only useful to test a single IP address for vulnerabilities and doesn't help a user determine whether their path to the Internet is being blocked.ProtocolGeek. The 'wording' for the Port Scan part of Network Utility seems to apply that it is scanning for TCP port status (and not UDP). Is this actually the case? I'm trying to diagnose if my L2TP VPN service on my OS X Server machine is open for business, and nothing is showing with Network Utility. (The PPTP port, which is TCP, as opposed to L2TP's UDP connection, shows up just fine.)If something like nmap is the answer, then I'll need some handholding on where to find it / run it (I expect via Terminal, which by itself is not too daunting, but at the moment 'man nmap' doesn't bring up anything.
Even this post is rather old, but it still comes up with the search results so I would like to reply a solution to the question.You can open the Terminal in Mac (type terminal on Spotlight) and then use NetCat command by typing like a sample below to test your specific port like this replacing 1xx with your target IP address, then the port to check.nc -vnzu 1xx.xxx.xxx.xxx 53or if you want to check a range of ports for example from port 1 to 53, just typenc -vnzu 1xx.xxx.xxx.xxx 1-53NetCat is already a built-in command in Mac so no need to install anything.Hope this helps. Apple Footer.This site contains user submitted content, comments and opinions and is for informational purposes only. Apple may provide or recommend responses as a possible solution based on the information provided; every potential issue may involve several factors not detailed in the conversations captured in an electronic forum and Apple can therefore provide no guarantee as to the efficacy of any proposed solutions on the community forums. Apple disclaims any and all liability for the acts, omissions and conduct of any third parties in connection with or related to your use of the site.
All postings and use of the content on this site are subject to the.
Comments are closed.